Dark Factory Gap: What Happens to Teams, Roles, and Organizations
In Part 1 of this series, we worked through the why: Shapiro's five levels of AI development, Brynjolfsson's J-Curve, and the core thesis that AI tools alone

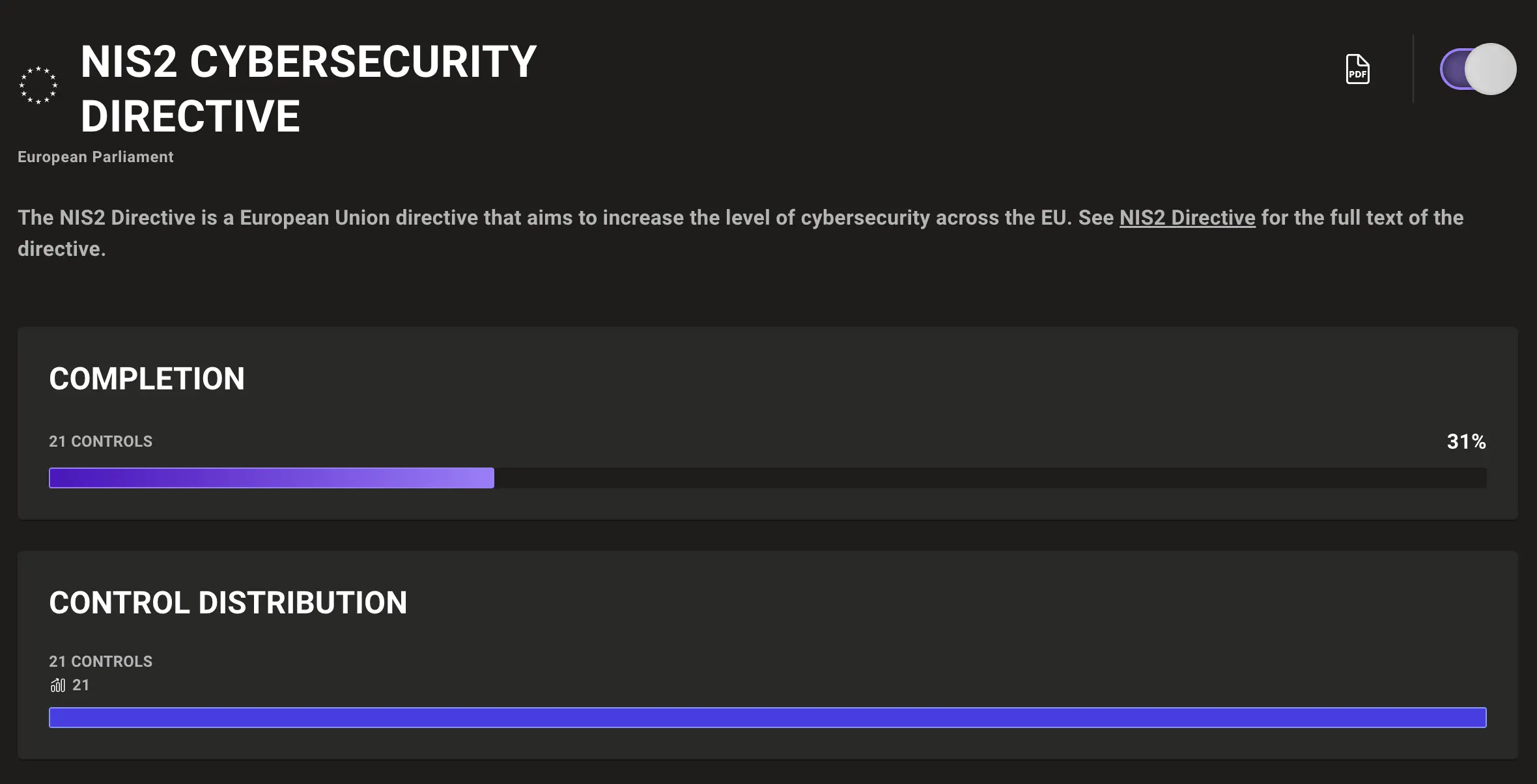
In the rapidly evolving world of software development, securing and managing the integrity of codebases is paramount, particularly for organizations subject to the NIS2 Directive. This EU regulation mandates robust cybersecurity practices to ensure the operational resilience and security of network and information systems. In this post, we'll explore how GitHub organizations can leverage Mondoo’s security platform to address specific NIS2 requirements effectively, focusing on key articles related to code management, access control, cybersecurity training, vulnerability handling, and incident notification.
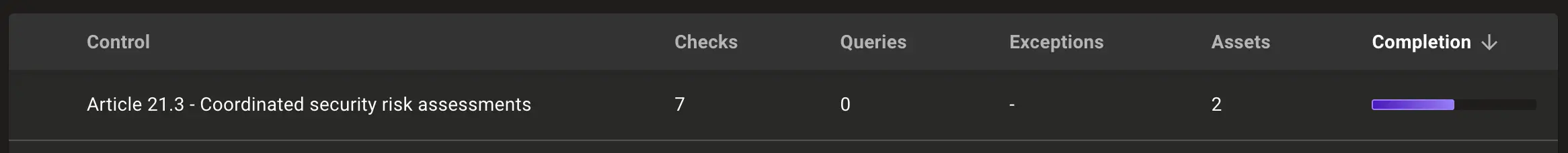
Under NIS2, particularly Article 21.3 and 21.2 I, organizations are required to manage security risks in a coordinated manner. For GitHub organizations, this means implementing rigorous controls around code changes and branch management. Mondoo aids in enforcing policies where each code update needs previous approvals to be dismissed, ensuring that only the most recent, reviewed changes are considered. This ensures that all reviews are based on the most current version of the code.
It also supports the requirement that all code branches must be updated before merging, reducing the risk of integrating outdated or vulnerable code.
To maintain branch integrity, force pushes should be denied. Disabling the "Force Push" option prohibits users from forcing their changes to the master branch, which ultimately prevents malicious code from entering source code.
Only specific individuals or teams should have the authority to push or merge code, which is crucial in maintaining the integrity of sensitive code areas. This includes enforcing that all code reviewers are strongly authenticated, ideally with Multi-Factor Authentication (MFA), and that any significant change to the code base, especially in sensitive areas, is approved by at least two authenticated administrators. In addition, accessing the package registry should also require MFA.
Organizations should have at least have two users with administrative permissions to maintain security and control. However, for the organization and package registry, the number of Administrators should be kept as low as possible.
An organization is advised to set code owners for every extremely sensitive code or configuration. Code owners are trusted users that are responsible for reviewing and managing an important piece of code or configuration.
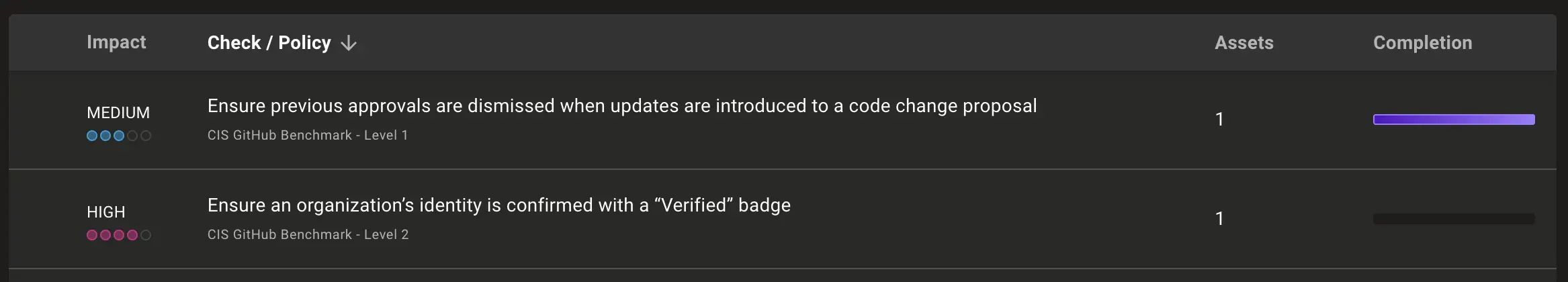
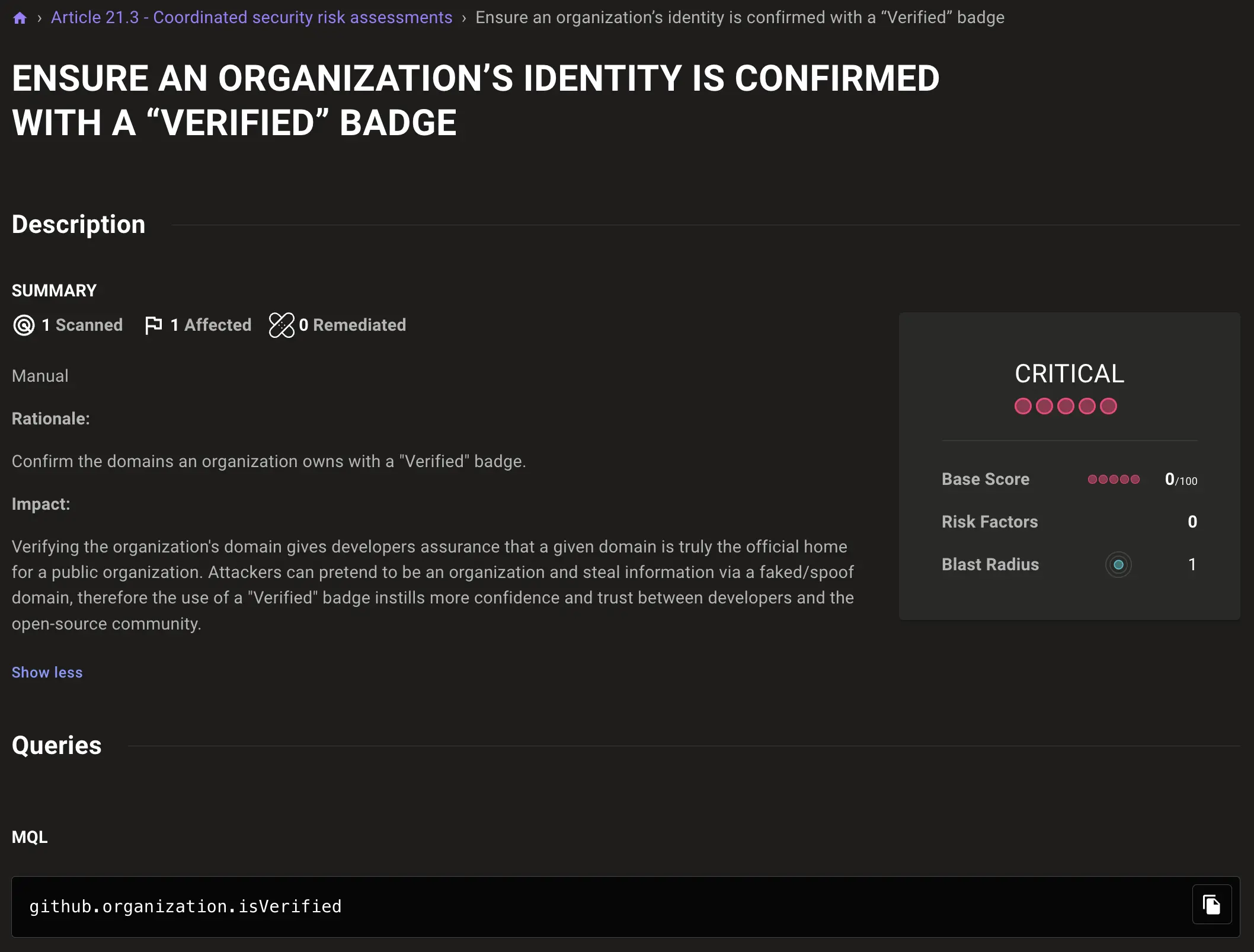
Before any new code is merged, all checks must pass. Additionally, having a “Verified” badge for the organization on GitHub confirms its identity, establishing trust and compliance with NIS2.
NIS2 emphasizes the importance of continuous cybersecurity training, as outlined in Article 21.2(g). This aspect is critical in ensuring that all team members are aware of the best practices and the latest security protocols. Mondoo aids in enforcing policies where access to critical assets, like the package registry, requires MFA, ensuring that only authorized, authenticated users can make changes. This limits the risk of unauthorized access and ensures that the handling of code and assets is only performed by personnel who understand the security implications.
With NIS2 now in effect, GitHub organizations need to adopt rigorous security measures to ensure compliance. One essential practice is the periodic review and archiving of inactive repositories. By regularly assessing and archiving repositories that are no longer active, organizations can reduce the risk posed by neglected projects, aligning with NIS2's focus on managing security risks.
In addition, all public repositories should include a SECURITY.md file. This file is crucial for documenting your security practices and providing contact information for security issues, ensuring transparency and compliance with NIS2 requirements.
Implementing vulnerability scanners for open-source packages is another critical step. These scanners help detect vulnerabilities in third-party components used within your projects, addressing potential risks proactively. Automating the scanning of packages for known vulnerabilities further supports this effort, keeping dependencies secure and up-to-date, which is a fundamental aspect of NIS2 compliance.
Branch protection is also a key requirement. Enforcing protection policies on the default branch prevents unauthorized changes and helps maintain the integrity of your codebase. This practice is in line with NIS2’s emphasis on secure code management.
Furthermore, it is essential to automate the scanning of code for risks whenever merging occurs. This ensures that new code meets security standards and does not introduce vulnerabilities, maintaining adherence to NIS2 guidelines.
Signing all artifacts in your releases provides a verifiable chain of trust, an important aspect of NIS2 compliance. This practice ensures that each release can be verified and trusted, which is crucial for maintaining the integrity of your software.
Strict base permissions for repositories are another critical measure. Setting these permissions ensures that only authorized users have access to sensitive areas of your codebase, protecting it from unauthorized modifications and aligning with NIS2’s security requirements.
Revoking anonymous access to artifacts is vital. By ensuring that only authenticated users can access sensitive data and intellectual property, you prevent unauthorized access and protect your organization’s assets, as mandated by NIS2.
Lastly, in the event of a security incident, rapid notification and response are crucial, as detailed in Article 23.1. Mondoo scans for the webhook configurations of repositories, preventing unauthorized data exposure and ensuring that all sensitive pipeline data is protected against leaks and breaches.
To support business continuity, outlined in Article 21.2(c), and robust incident handling as per Article 21.2(b), Mondoo continuously scans for the inclusion of sensitive data within pipeline files. This ensures that accidental commits of sensitive information do not compromise the security of the organization.
Achieving compliance with the NIS 2 Directive through Mondoo involves several strategic implementations tailored to enhance security and manage risks effectively within your GitHub organization. Here’s a practical approach to integrating Mondoo into your compliance strategy:
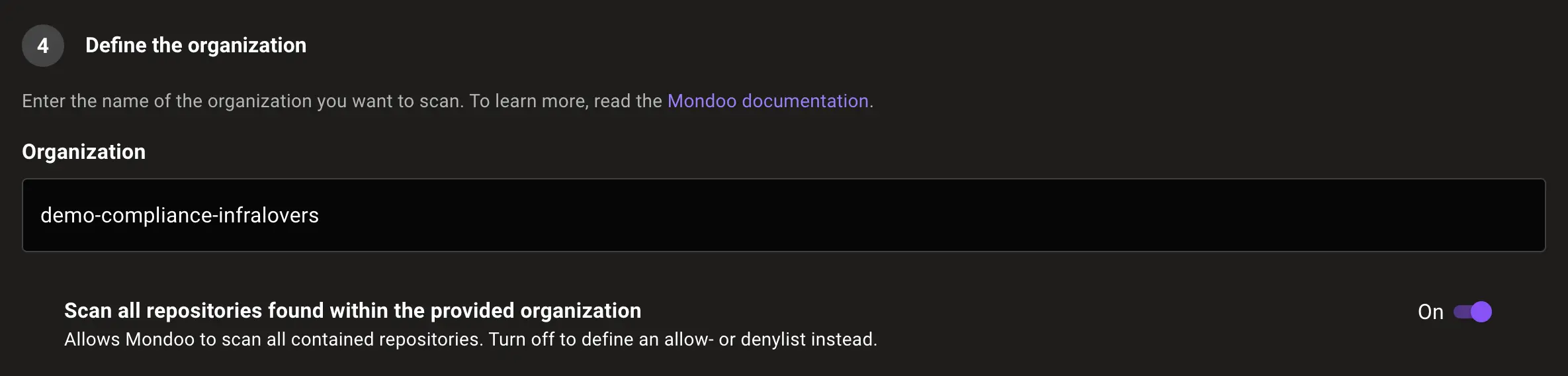
By following these steps, you can leverage Mondoo to not only meet the stringent requirements of the NIS 2 Directive but also enhance the overall security posture of your GitHub organization. This strategic approach ensures that you are well-prepared to handle the evolving cybersecurity landscape while maintaining high standards of operational resilience.
Achieving compliance with NIS2 is not just about checking a box but ensuring that the security measures put in place are effective and resilient. By utilizing Mondoo's capabilities, GitHub organizations can ensure their development environments align with NIS2 directives, safeguarding their assets and ensuring continuity in their operations. This not only meets regulatory requirements but also builds trust with customers and stakeholders, which is crucial in today’s digital economy. Note that Mondoo can be used to get compliant with more compliance frameworks and integration types! If you are interested in enhancing your GitHub security posture, make sure to check out our blogpost about Leveraging Mondoo for Vulnerability Detection in GitHub!
You are interested in our courses or you simply have a question that needs answering? You can contact us at anytime! We will do our best to answer all your questions.
Contact us