Sources of Secrets by HashiCorp Vault - Revisited
Same Goal, Different Pattern In the previous article we synchronized 1Password items into Vault by pulling data with Terraform and writing it into a KV engine.

This article shows you how to secure your Kubernetes cluster with the Mondoo Operator. The Mondoo Operator simplifies the process of securing your Kubernetes workloads by automatically deploying the Mondoo security agent on your cluster nodes to scan for vulnerabilities and compliance issues. In comparison to the Mondoo GitHub Action, the Mondoo Operator is a more advanced and automated way to secure your Kubernetes workloads. The operator also provides a more comprehensive view of your cluster's security posture by continuously scanning your workloads for vulnerabilities and compliance issues - including containers and nodes.
The operator also includes an admission controller that can enforce security policies on your cluster. This ensures that only secure workloads are deployed to your cluster. The Mondoo Operator is a powerful tool for securing your Kubernetes workloads and ensuring that your cluster is secure and compliant.
We will concentrate on the scan of Kubernetes workloads that are already running in your cluster. This is a common use case to ensure that your production workloads are secure and compliant. So the admission controller will be covered in an upcoming article.
At the moment the Mondoo Operator can be installed by the following approaches:
The manifest based installation is the simplest way to install the Mondoo Operator, but we gonna concentrate on the helm approach. The following manifest installs the Mondoo Operator in the mondoo namespace:
1helm repo add mondoo https://mondoohq.github.io/mondoo-operator
2helm repo update
3helm install mondoo-operator mondoo/mondoo-operator --namespace mondoo-operator --create-namespace
The Mondoo Operator needs authentication configuration to the Mondoo API. So you need to create dedicated secrets to your related Mondoo Spaces by Service Accounts. You can create the service accounts through the ui as the documentation of mondoo describes. You can download the according json definition for the account. The following example shows how to create a secret for the Mondoo Operator based on that json definition:
1kubectl create secret generic mondoo-secret-k8score-space --namespace mondoo-operator --from-file=config=mondoo-service-account.json
The Mondoo Operator can be configured by a MondooAutoConfig custom resource. The following example shows a MondooAuditConfig that configures the Mondoo Operator:
1apiVersion: k8s.mondoo.com/v1alpha2
2kind: MondooAuditConfig
3metadata:
4 name: mondoo-client
5 namespace: mondoo-operator
6spec:
7 mondooCredsSecretRef:
8 name: mondoo-secret-k8score-space
9 admission:
10 enable: false
11 consoleIntegration:
12 enable: true
13 containers:
14 enable: true
15 schedule: 0 * * * *
16 kubernetesResources:
17 enable: true
18 schedule: 0 */2 * * *
19 nodes:
20 enable: true
21 schedule: 0 0 * * *
22 style: cronjob
23 filtering:
24 namespaces:
25 include:
26 - default
27 - kube-system
28 - monitoring
29 - logging
30 exclude:
31 - kube-public
Our sample configuration includes the scanning of nodes, kubernetes resources. The configuration can be applied by the following command:
1kubectl apply -f mondoo-config.yaml
If you want to define any further scanning for workload of teams that have their own Mondoo Space, you just need to define the MondooAuditConfig for that space referncing their credentials secrect. The following example shows how to configure the Mondoo Operator for a specific team with their credentials:
1kubectl create secret generic mondoo-secret-k8s_team_a-space --namespace mondoo-operator --from-file=config=mondoo-service-account-team-a.json
And a custom definition of the MonddoAuditConfig for that team:
1apiVersion: k8s.mondoo.com/v1alpha2
2kind: MondooAuditConfig
3metadata:
4 name: mondoo-client-team-a
5 namespace: mondoo-operator
6spec:
7 mondooCredsSecretRef:
8 name: mondoo-secret-k8s_team_a-space
9 admission:
10 enable: false
11 nodes:
12 enable: false
13 consoleIntegration:
14 enable: false
15 containers:
16 enable: true
17 schedule: 0 * * * *
18 kubernetesResources:
19 enable: true
20 schedule: 0 */2 * * *
21 filtering:
22 namespaces:
23 include:
24 - team-a-app
25 - team-a-app2
The Mondoo Operator provides a visualisation of the security status of your Kubernetes workloads. The visualisation is available in the Mondoo console. The following screenshot shows an example of the visualisation of the security status of a Kubernetes cluster from the view of a Mondoo Space:
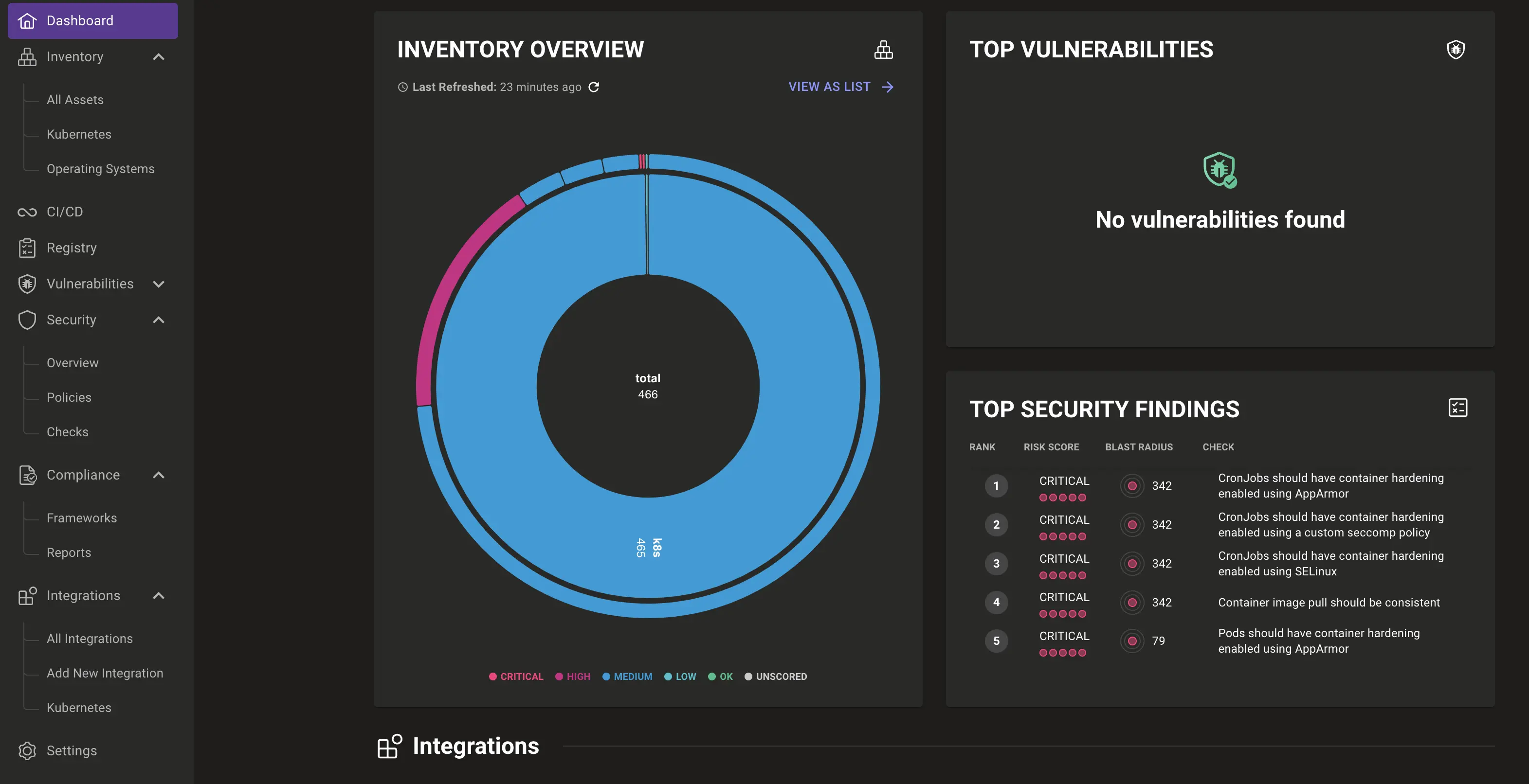
You can zoom into multiple objects by going through all the relationships that are established across the cluster objects, starting with the Inventory
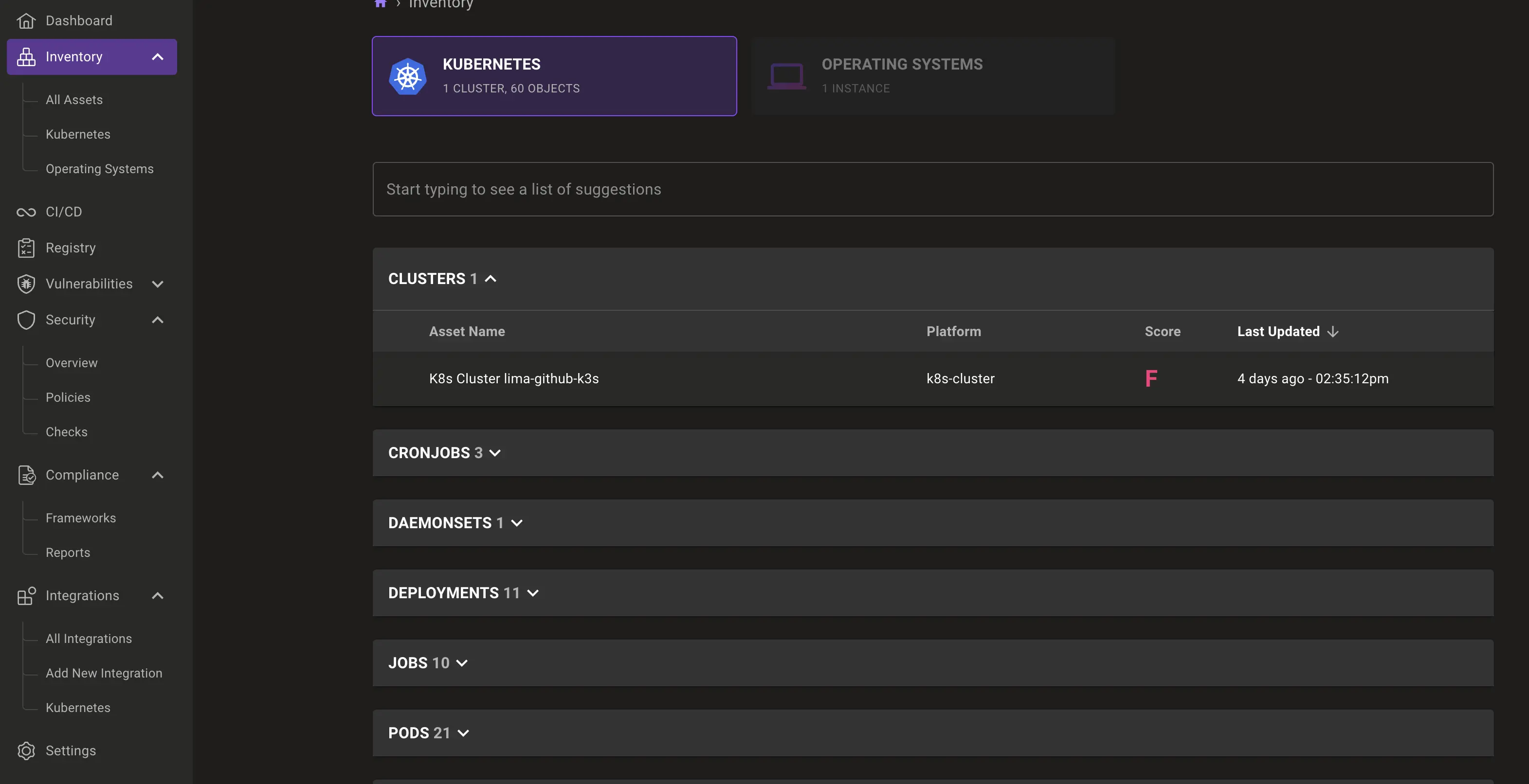
We have selected the Traefik service to start our review of this data visualisation:
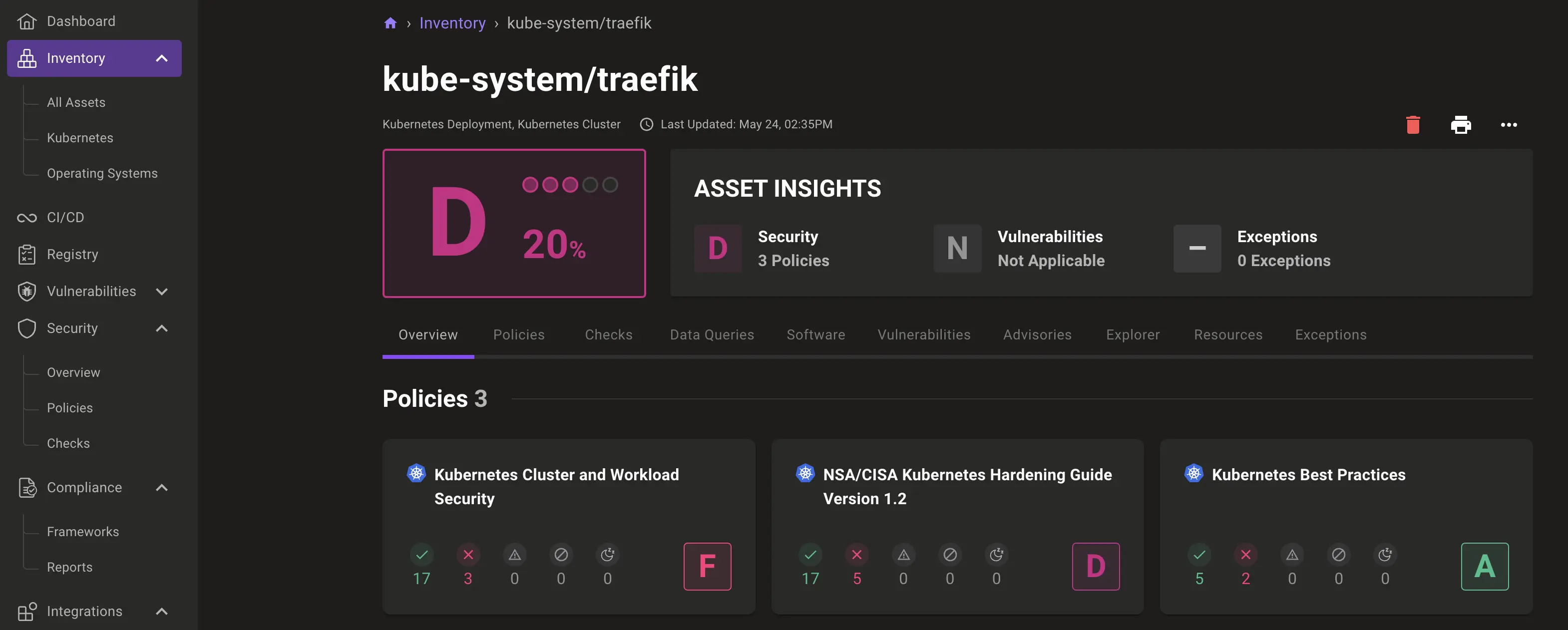
On the Explorer tab, you can display related objects - i.e. the corresponding replica set for the Traefik service:
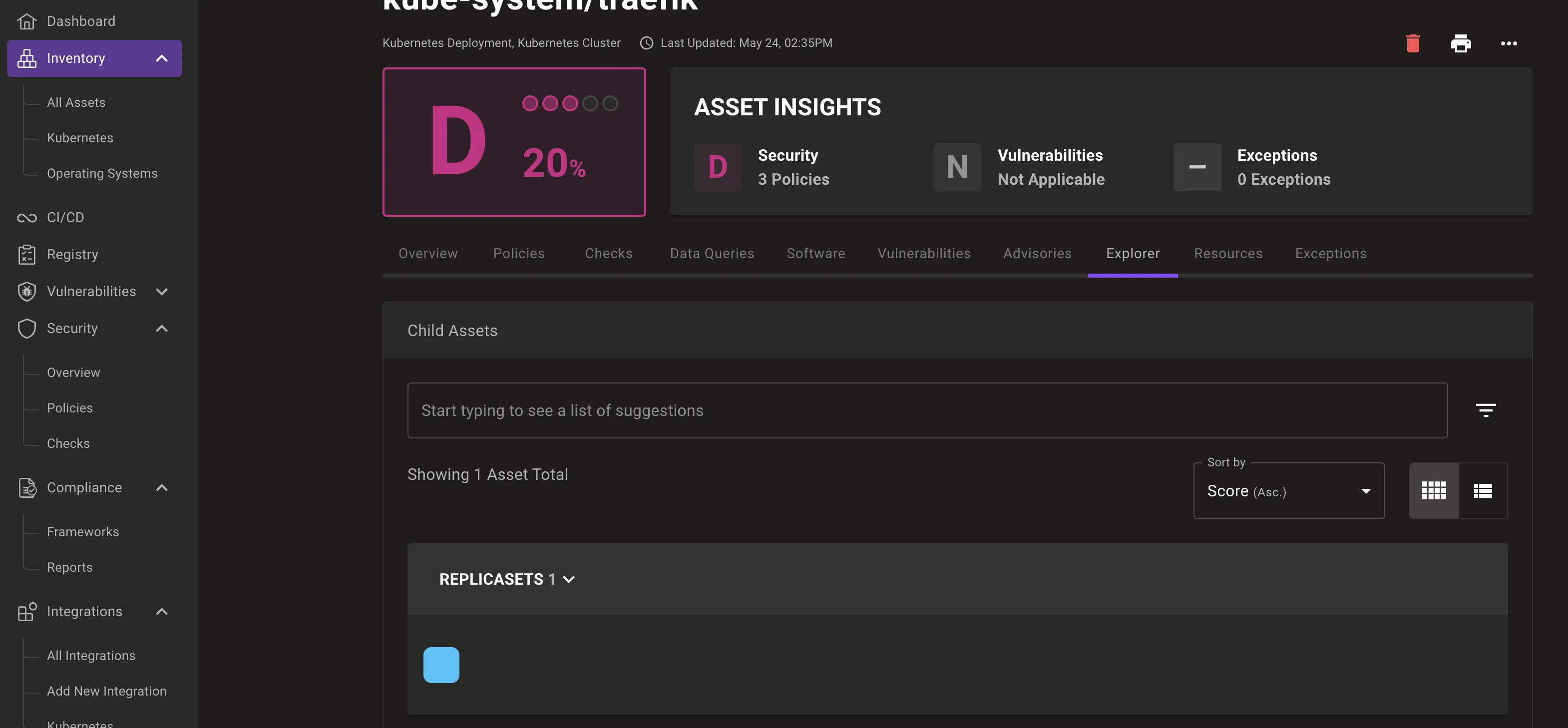
Click on the colourful blob to follow this resource to your scan result
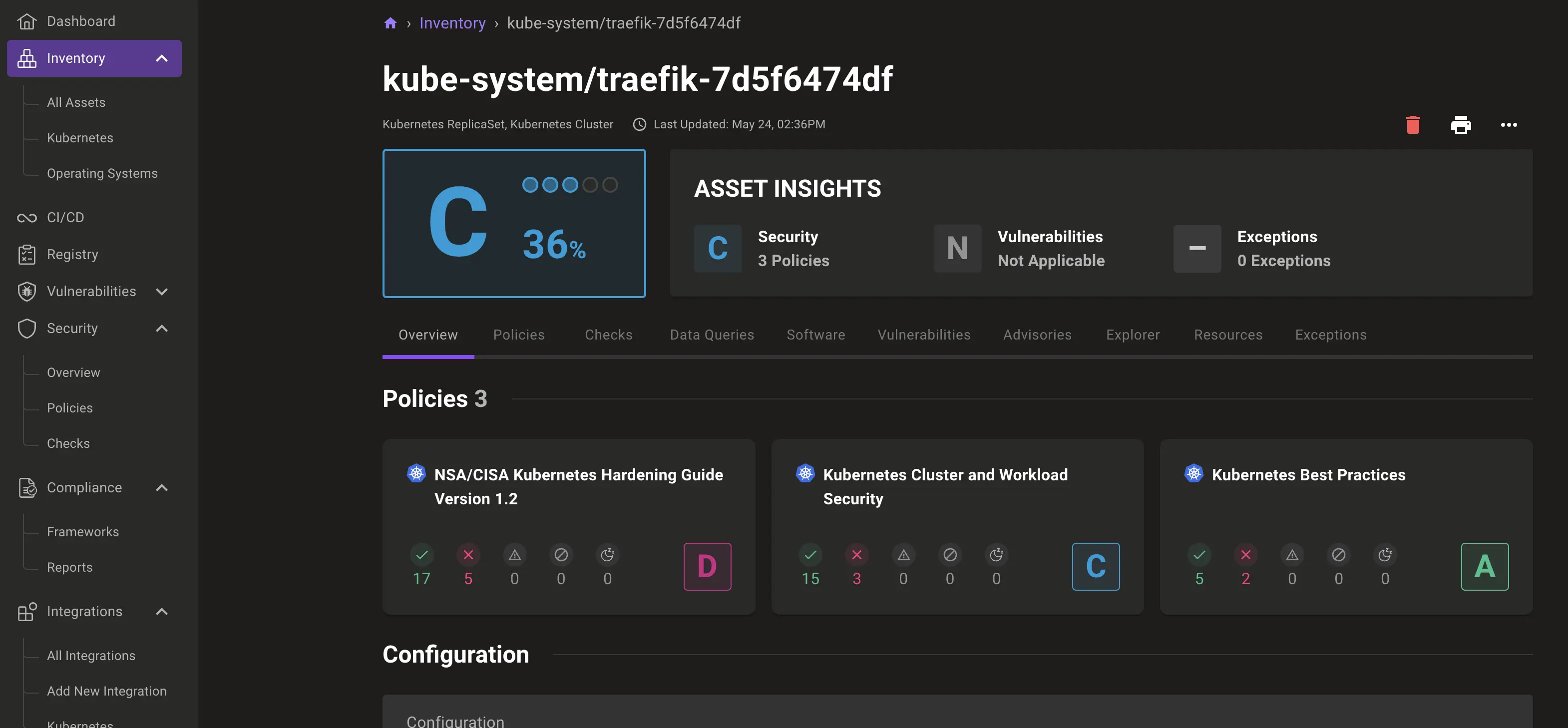
And from Traefik's replica set, we can also see the associated pods:
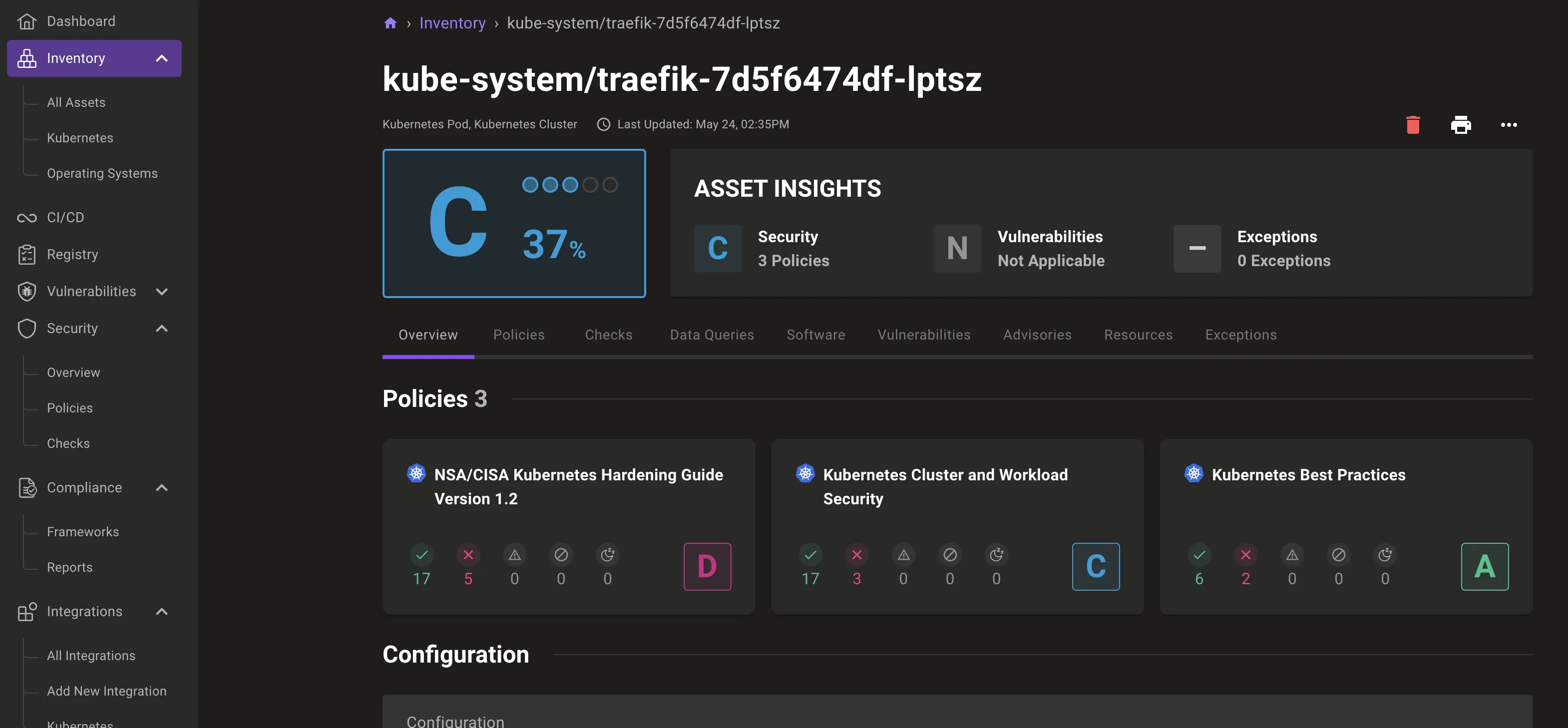
So with this nice visualisation, you can easily navigate through your Kubernetes objects and view the security status of your workloads.
The Mondoo Operator is a powerful tool for securing your Kubernetes workloads. It simplifies the process of securing your Kubernetes workloads by automatically deploying the Mondoo security agent on your cluster nodes to scan for vulnerabilities and compliance issues. The operator also provides a more comprehensive view of your cluster's security posture by continuously scanning your workloads for vulnerabilities and compliance issues - including containers and nodes. The Mondoo Operator is a powerful tool for securing your Kubernetes workloads and ensuring that your cluster is secure and compliant.
In the configuration samples above, we have shown how to configure the Mondoo Operator for scanning Kubernetes workloads based on the requirements for different use cases. As an operator of a kubernetes cluster i want to ensure that my production workloads are secure and compliant. This requires also scanning of the nodes, containers and kubernetes resources. Nodes and containers cannot be scanned by the Mondoo GitHub Action, so the Mondoo Operator is the right tool for this job.
Teams that own their own Mondoo Space can also configure the Mondoo Operator for their specific requirements. This allows them to scan their workloads based on their requirements and ensures that their workloads and definitions are secure and compliant.
In the next article we will cover the admission controller of the Mondoo Operator. This is a powerful feature that can enforce security policies on your cluster.
Stay tuned!
You are interested in our courses or you simply have a question that needs answering? You can contact us at anytime! We will do our best to answer all your questions.
Contact us