Sources of Secrets by HashiCorp Vault - Revisited
Same Goal, Different Pattern In the previous article we synchronized 1Password items into Vault by pulling data with Terraform and writing it into a KV engine.

As the world's leading platform for software development and collaboration, GitHub sees millions of new repositories created every day. While this rapid growth fosters innovation, it also presents security challenges. Without proper oversight, newly created repositories can inadvertently harbour vulnerabilities that threaten the integrity of your codebase and compromise your organisation's security posture. In this blog post, we'll explore how Mondoo, a powerful security tool, can play a crucial role in identifying and mitigating these vulnerabilities, ensuring that your GitHub repositories remain secure from the moment they are created.
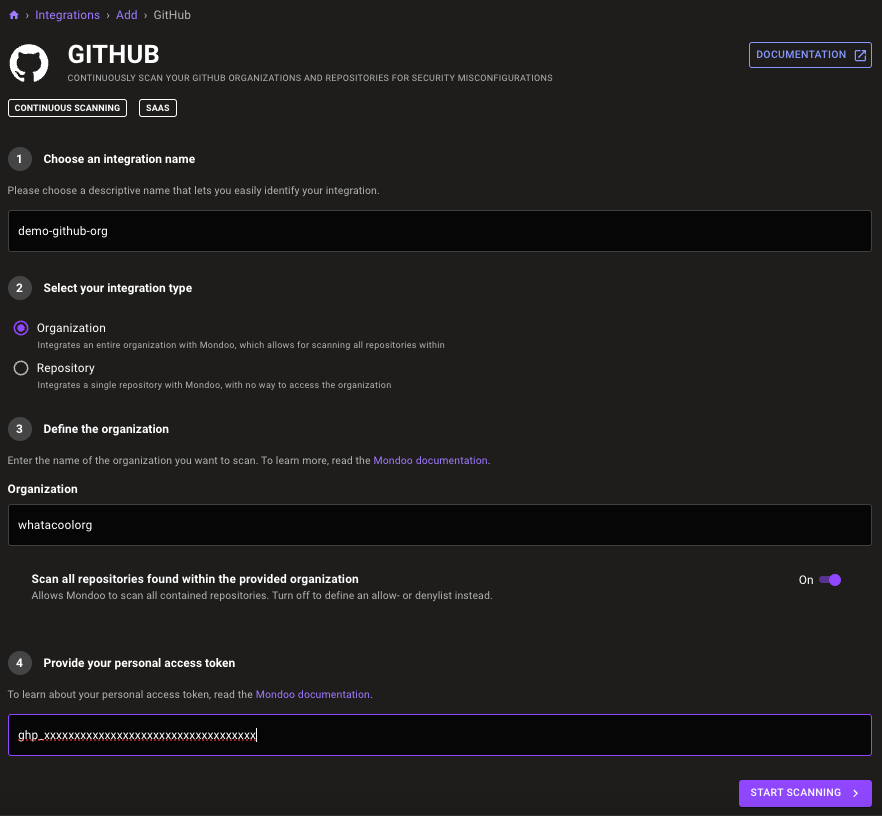
Start by integrating your GitHub repository or organisation with Mondoo. You will need a Mondoo organisation and a personal GitHub access token for your user. There are several ways to add your GitHub assets to Mondoo.
Add GitHub as a new integration to your space. You can add individual repositories or the whole organisation, specifying whether you want to scan all repositories or set an allow or deny list:
You can use cnspec to scan your entire organisation or a single repository within the organisation. To do this, install cnspec and login to the correct space and export the GitHub token:
$ export GITHUB_TOKEN=<your personal access token>
$ cnspec scan github org <ORG_NAME>
$ cnspec scan github repo <ORG_NAME/REPO_NAME>
This Terraform resource enables continuous scanning of GitHub organisations and repositories. To add it, you can use the GitHub integration provider from the Terraform registry.
Have a look at our blog about the use of Mondoo with Terraform.
Policies in the context of Mondoo and cnspec serve as a set of specifications used during system scans. They act as checklists to ensure that systems comply with security standards and best practices. They are guidelines encoded in a highly readable format that cnspec can understand and execute.
If you haven't already added policies for GitHub, you can do so by navigating to the Registry tab in your Mondoo space. It is recommended that you enable all policies.
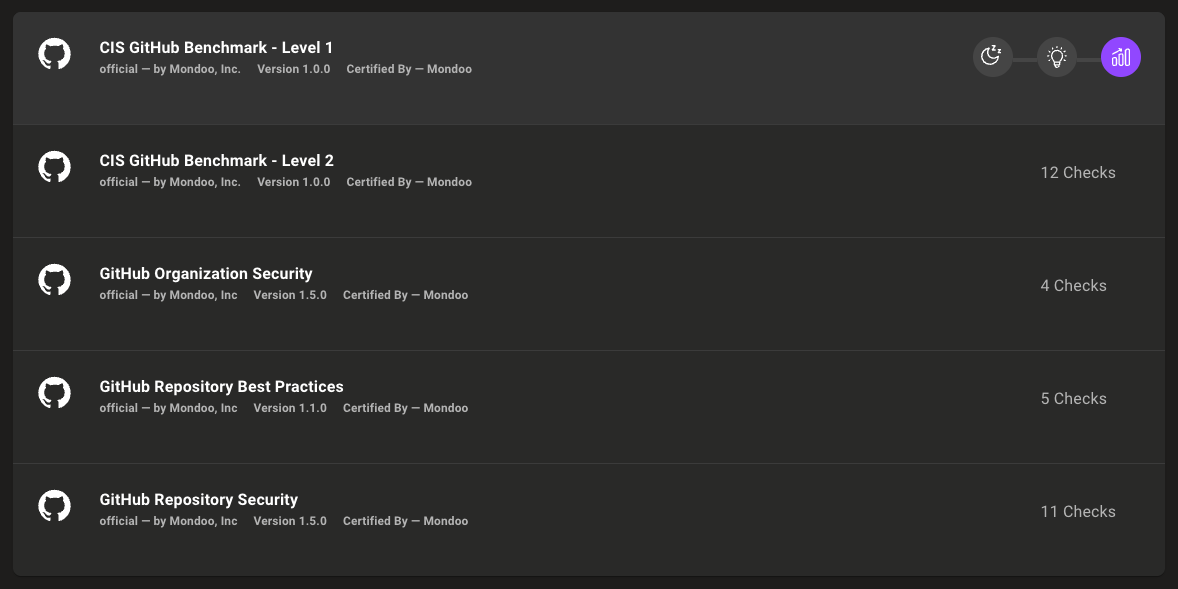
The policies applied are displayed within the scanned asset entry in the Dashboard and determine its overall security score. Clicking on a policy displays all the checks that have either passed or failed. Each check offers detailed insights into the scanning process and provides suggestions for mitigating vulnerabilities discovered.
Visible policies and the number of checks in policies may vary depending on the asset type (github-repo / github-org).
Query Packs are collections of pre-defined queries designed to inspect different aspects of systems or assets. These packs are useful for running multiple queries together, simplifying the process of gathering information about your infrastructure's security posture, compliance status, or other relevant metrics.
Add query packs from the Registry tab of your Mondoo space.
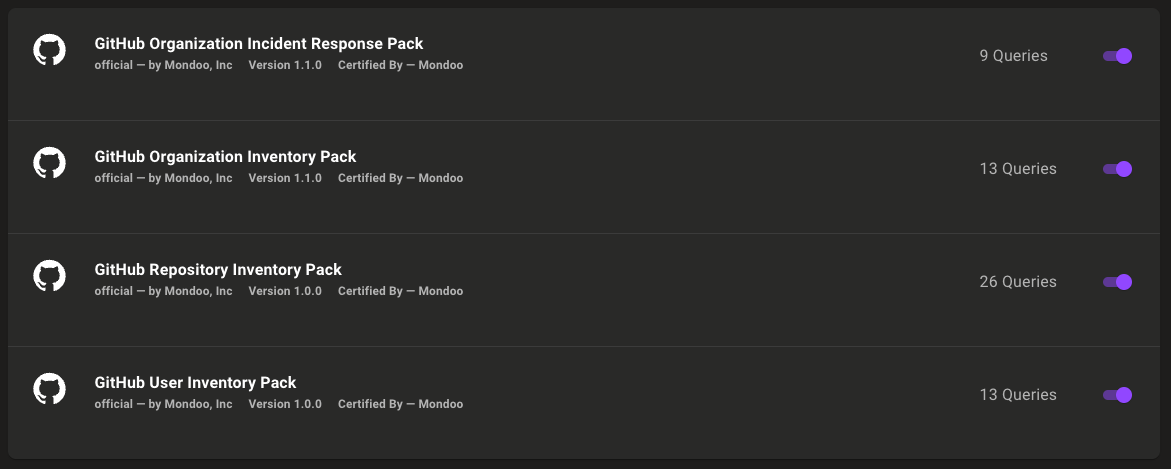
Query packs can be run with the cnquery CLI tool:
$ export GITHUB_TOKEN=<your personal access token>
$ cnquery scan github org <org_name>
$ cnquery scan github repo <owner>/<repo>
$ cnquery scan github user <user_name>
Query packs can also be downloaded and used locally, for example:
$ cnquery scan github user <user_name> -f mondoo-github-inventory.mq.yaml
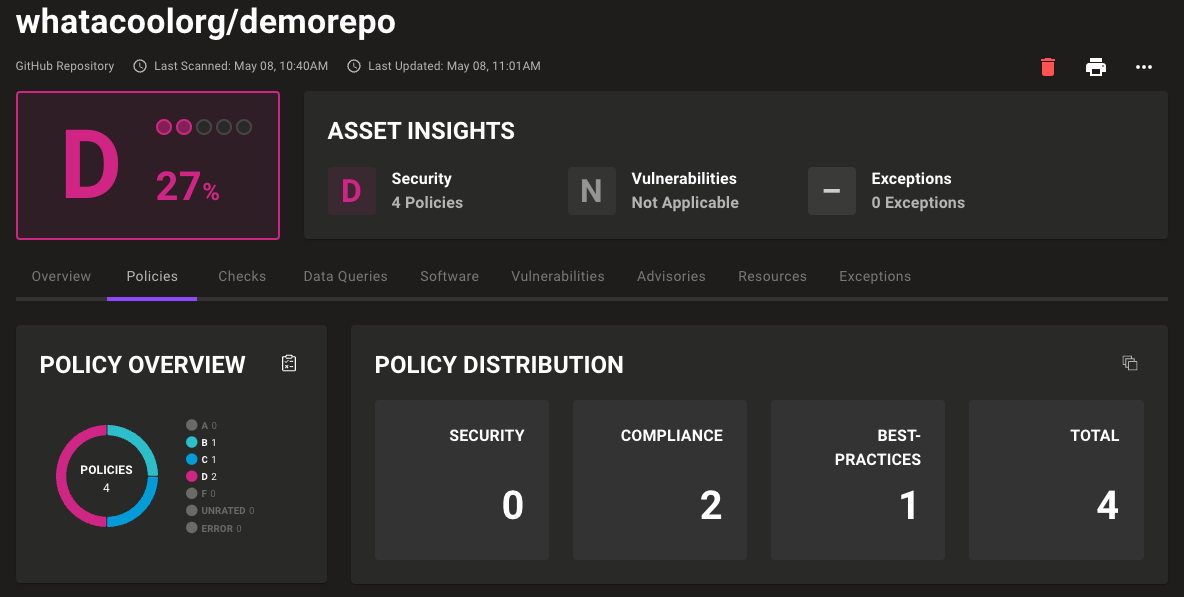
In this scenario, a new user and organisation, and a new repository within that organisation, have been created with no additional settings, so the scan results may be different to yours. The integration was set up as a GitHub organisation using the dashboard.
For a new organisation with no additional settings as in this case, the score is not as favourable as it could be.
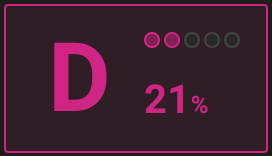
Mondoo streamlines the process of identifying and addressing failed checks. The dashboard provides a comprehensive overview of all checks within the Checks tab, along with suggested actions for the most critical failures. This tab displays the results of each individual check performed on enabled policies. The dashboard allows users to filter the checks displayed to show those that have failed first, providing an efficient way to review them. By expanding a check, users can gain further insight into the query being tested, as well as the expected and returned results. Further description and recommended solutions help to understand the implications.
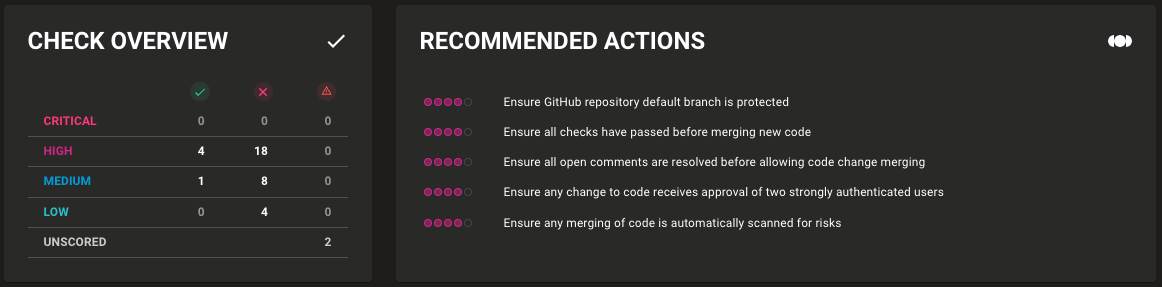
In this case, the repository asset and the organisation asset have multiple vulnerabilities.
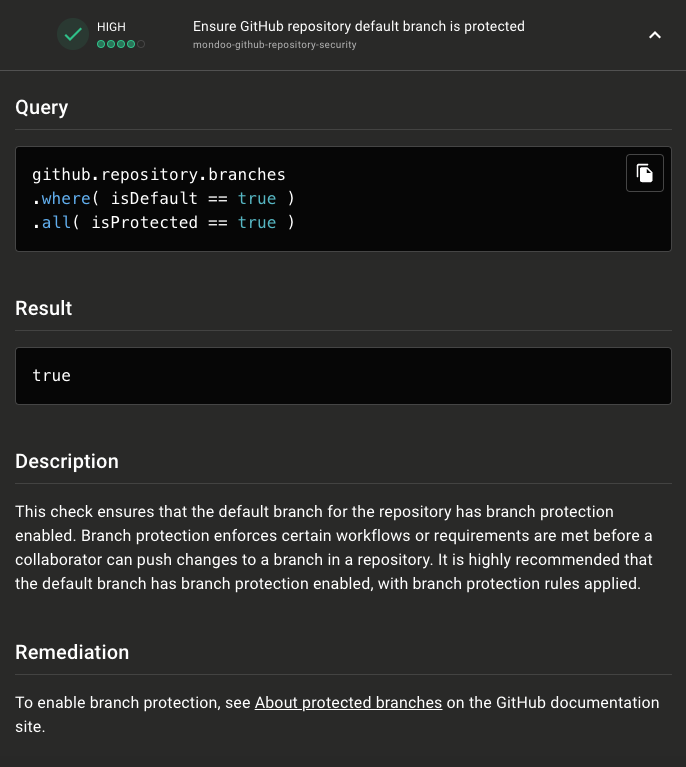
To resolve failed checks, Mondoo provides either detailed information and steps or links to the appropriate documentation on how to resolve the issue.
For example, within policies such as "CIS GitHub Benchmark - Level 1" and "GitHub Repository Security":
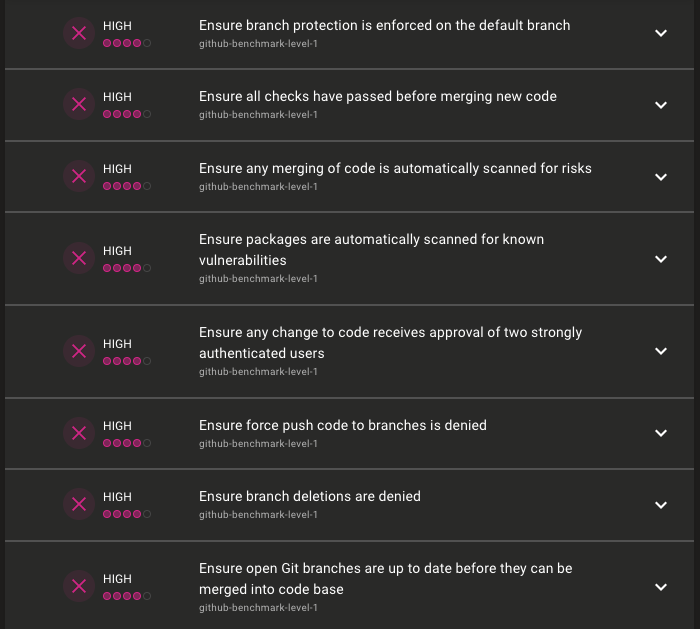
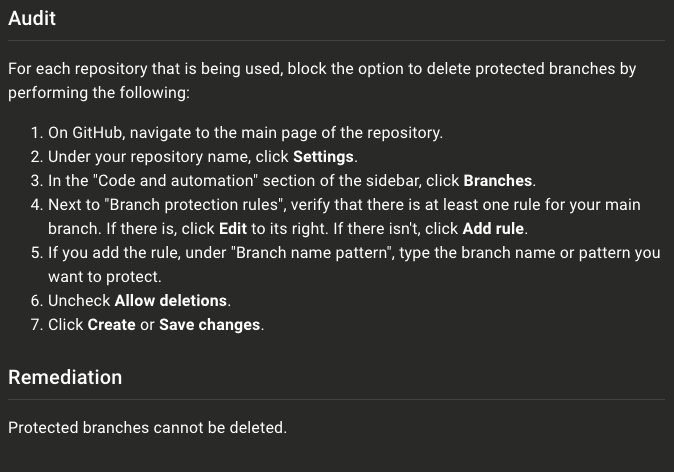
Following these remediation steps for the policies in the example above, the asset score improved from D to A! Repeating these remediation steps for additional policies will result in a higher score and a stronger security posture for your GitHub organisation.

Fortunately, GitHub already provides a basic level of security by default. In the case of GitHub organisations or repositories, most serious vulnerabilities can be mitigated by enabling branch protection rules. However, it is advisable to additionally verify that the following common vulnerabilities and high-priority checks are in place:
In addition, GitHub Code Scanning can be used to improve the security and quality of the code in your GitHub repositories. This feature makes it possible to automatically check the code for security risks and errors. It aims to recognize and rectify potential vulnerabilities at an early stage.
You are interested in our courses or you simply have a question that needs answering? You can contact us at anytime! We will do our best to answer all your questions.
Contact us